Netwerk: verschil tussen versies
(→VLANs) |
Geen bewerkingssamenvatting |
||
| (2 tussenliggende versies door dezelfde gebruiker niet weergegeven) | |||
| Regel 121: | Regel 121: | ||
**vlan 1336 (dhcp-server) | **vlan 1336 (dhcp-server) | ||
**vlan 1337 (dhcp-server) | **vlan 1337 (dhcp-server) | ||
== Firewall == | |||
Reject traffic from guest VLANs (villanova & HSN) to management VLAN: | |||
* Firewall/NAT -> Firewall/NAT Groups -> create "management" group, then Actions -> Config and set network "10.138.64.0/24" and save | |||
* Firewall Policies -> Add ruleset "GUEST_NET_LOCAL" : | |||
** Description "Guest to router" | |||
** Default action DROP | |||
** add rule 1 "allow DNS" action Accept protocol TCP+UDP destination port 53 | |||
** add rule 2 "allow DHCP" action Accept protocol UDP destination port 67 | |||
** go to Interfaces and add switch0.1336 direction local, and switch0.1337 direction local | |||
* Firewall Policies -> Add ruleset "GUEST_NET_IN" | |||
** Description "From villanova/HSN nets" | |||
** Default action ACCEPT | |||
** add rule 1 "drop guestnet to mgmt" action Drop protocol All protocols destination network group Management subnet | |||
** go to Interfaces and add switch0.1336 direction In, and switch0.1337 direction In | |||
Now, hosts on villanova & HSN nets can use DHCP and DNS, but nothing else on the router; also, they can't access the management subnet at all. | |||
=Aruba Accesspoints= | =Aruba Accesspoints= | ||
| Regel 132: | Regel 150: | ||
*hij moet nu een lease krijgen in het management-subnet | *hij moet nu een lease krijgen in het management-subnet | ||
*hij vindt dan automatisch zijn controller, en biedt dezelfde netwerken aan | *hij vindt dan automatisch zijn controller, en biedt dezelfde netwerken aan | ||
==Individuele settings== | |||
Op de controller zijn alle APs online. Maak een nieuw wired network genaamd "passthrough" met: | |||
*Primary usage employee | |||
*PoE enabled | |||
*Admin status Up | |||
*Mode Access | |||
*Client IP Network Assigned | |||
*Access VLAN 1336 (villanova) | |||
*VLAN Assignment Rule "If AP-Name equals AP233 assign VLAN 1337" (AP233 is de accesspoint waar de netwerkkabel naar ons atelier doorheen lust) | |||
Stel "passthrough" in op alle wired poortjes behalve 0/0 (die blijft op default_wired_port_profile). | |||
Huidige versie van 1 okt 2022 om 12:41
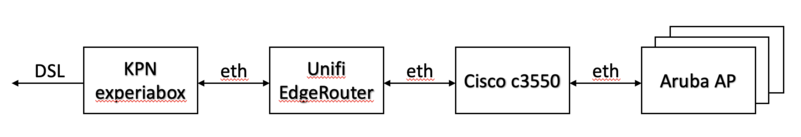
Deze pagina omschrijft de netwerkinfrastructuur aan de Villa Novastraat.
Overview
TODO
- Backup configs
- Note passwords somewhere outside of this wiki
- Villanova network
- Install second AP in the hallway
- Install third AP in the hallway
- Wired connection to space
- Wired connection to Harm
- Spacenet
VLANs
- 1 - catchall
- geen dhcp-server
- 64 - management
- dhcp-server op edgerouter
- 10.138.64.0/24
- 10.138.64.1 edgerouter
- 1336 - villanova
- dhcp-server op edgerouter
- 10.138.65.0/24
- 10.138.65.1 edgerouter
- 1337 - hsn
- dhcp-server op edgerouter
- 10.138.66.0/24
- 10.138.66.1 edgerouter
Cisco C3550
- DHCP client on vlan 64
- No IP on all other VLANs
- Telnet/SSH enabled
Fix PoE port resetting
The Cisco switch power cycles PoE ports when the link goes down or takes too long to come up, causing the Aruba APs to keep powercycling without coming up.
To fix this:
Switch>enable Switch#configure terminal Switch(config)#interface range FastEthernet 0/1-24 Switch(config-if-range)#power inline delay shutdown 20 initial 300
This saves it to running-config, but because of a bug, the running-config does not actually show it when you run "show running-config". Instead, use "show running-config all" (which also shows the defaults) to display the values, even though they are not defaults.
NOTE: to make this config persistent, you need to run "copy running-config startup-config all". The 'all' circumvents the bug above. After this, "show startup-config" also shows the necessary PoE settings and the switch reboots correctly.
Ports
- 1 --> unifi edgerouter x
- vlan 1 (untagged)
- vlan 64
- vlan 1336
- vlan 1337
- 2 --> accesspoint villanova2
- poe enabled met 300 seconds initial
- vlan 1 (untagged)
- vlan 64
- vlan 1336
- vlan 1337
- 3 --> accesspoint villanova4
- poe enabled met 300 seconds initial
- vlan 1 (untagged)
- vlan 64
- vlan 1336
- vlan 1337
- 4 --> accesspoint villanova6
- poe enabled met 300 seconds initial
- vlan 1 (untagged)
- vlan 64
- vlan 1336
- vlan 1337
- 5 --> kabel naar hsn
- vlan 1337 untagged
- 6 --> kabel naar hsn
- vlan 1337 untagged
- 7 --> kabel naar harm
- vlan 1336 untagged
- 24 --> management vlan
- vlan 64 tagged
Unifi Edgerouter X
- dhcp servers:
- let erop dat je de pool start/end moet invullen, anders is de pool size 0 en krijg je geen leases
- mgmt 10.138.64.0/24
- villanova 10.138.65.0/24
- hsn 10.138.66.0/24
- in de config tree: service -> gui -> listen-address "10.138.64.1" zodat ie alleen bereikbaar is via management vlan
Ports
- eth0 wan --> kpnrouter
- dhcp client
- eth1 lan --> cisco poe port 1 trunkport
- vlan 1 (untagged)
- vlan 64 (dhcp-server)
- vlan 1336 (dhcp-server)
- vlan 1337 (dhcp-server)
- eth2
- vlan 1 (untagged)
- vlan 64 (dhcp-server)
- vlan 1336 (dhcp-server)
- vlan 1337 (dhcp-server)
- eth3
- vlan 1 (untagged)
- vlan 64 (dhcp-server)
- vlan 1336 (dhcp-server)
- vlan 1337 (dhcp-server)
- eth4
- vlan 1 (untagged)
- vlan 64 (dhcp-server)
- vlan 1336 (dhcp-server)
- vlan 1337 (dhcp-server)
Firewall
Reject traffic from guest VLANs (villanova & HSN) to management VLAN:
- Firewall/NAT -> Firewall/NAT Groups -> create "management" group, then Actions -> Config and set network "10.138.64.0/24" and save
- Firewall Policies -> Add ruleset "GUEST_NET_LOCAL" :
- Description "Guest to router"
- Default action DROP
- add rule 1 "allow DNS" action Accept protocol TCP+UDP destination port 53
- add rule 2 "allow DHCP" action Accept protocol UDP destination port 67
- go to Interfaces and add switch0.1336 direction local, and switch0.1337 direction local
- Firewall Policies -> Add ruleset "GUEST_NET_IN"
- Description "From villanova/HSN nets"
- Default action ACCEPT
- add rule 1 "drop guestnet to mgmt" action Drop protocol All protocols destination network group Management subnet
- go to Interfaces and add switch0.1336 direction In, and switch0.1337 direction In
Now, hosts on villanova & HSN nets can use DHCP and DNS, but nothing else on the router; also, they can't access the management subnet at all.
Aruba Accesspoints
Setup
- hang aan HSN-poortje (5/6) en wacht tot ie een lease krijgt in het HSN-subnet
- log in op de controller, klik op AP -> Configuration -> Edit -> Uplink -> management vlan is 64
- maintenance -> reboot -> AP -> reboot selected
- reboot --> na de reboot, trek hem uit poortje 5/6 en zet hem in poortje 2/3/4 (de AP-poortjes)
- hij moet nu een lease krijgen in het management-subnet
- hij vindt dan automatisch zijn controller, en biedt dezelfde netwerken aan
Individuele settings
Op de controller zijn alle APs online. Maak een nieuw wired network genaamd "passthrough" met:
- Primary usage employee
- PoE enabled
- Admin status Up
- Mode Access
- Client IP Network Assigned
- Access VLAN 1336 (villanova)
- VLAN Assignment Rule "If AP-Name equals AP233 assign VLAN 1337" (AP233 is de accesspoint waar de netwerkkabel naar ons atelier doorheen lust)
Stel "passthrough" in op alle wired poortjes behalve 0/0 (die blijft op default_wired_port_profile).